No, I Can’t Stop Your Spam (Part 3)
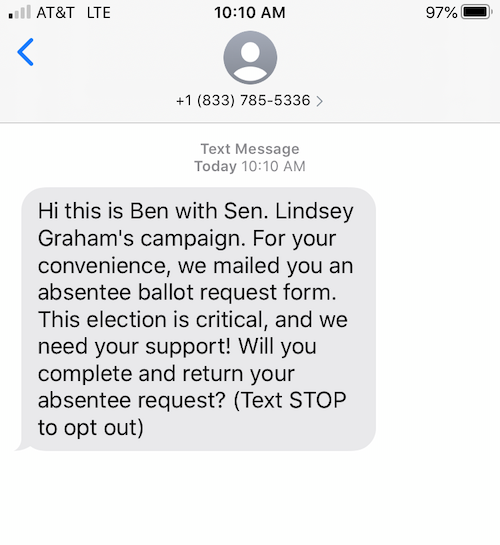
My better half and I have been suddenly getting quite a few spam phone messages in the last month. I’ve titled it part 3 because I’ve posted about it several times before1,2. I’ll make this one a bit more comprehensive so that, hopefully, it’s my last on the topic. I’ve been guessing that the recent spam is mostly related to the political season or that fact that AT&T is now pimping an add-on paid service to stop robocalls. We both got a spam text message ‘notifying’ us that Senator Lindsey Graham is mailing us absentee ballots and today I got this voice mail yesterday morning:
At least they could have narrowed their spam list down to folks who need braces for pain relief and mobility. And I suppose registering as an independent didn’t help. I had been bragging for years that I receive barely any unsolicited phone calls or emails. We have both of our phone numbers on the Do Not Call Registry3 but it seems that our officials are more concerned with the idea that TikTok and WeChat are foreign advisaries4. My brother’s voicemail message says something to the extent of “No, this is not Miquel. I don’t need any insurance, I don’t have any debts, I won’t vote for you if you’re calling me, and I’ll block your number if you don’t leave a voicemail”. Judging by the number of complaints I’ve heard over the last ten years, this isn’t a problem that will solve itself simply because our economy is geared towards getting our attention and changing our behavior.
I mean, technically, the practice goes all the way back to 1864, when a mass telegram was sent advertising a dentist5. It wan’t called spam until the internet crowd related it to the Monty Python sketch6. Nowadays, it seems folks have just kind of accepted and even practice it themselves with group text messages soliciting events, products, and whatever else. Even those planes flying above your heads at beaches are just spam. App spam prevails with those little notifications beeps and icons. There’s email spam, mail spam, phone spam, search engine spam, social media spam, air message sign spam, political spam, text spam, gas station spam, spam, spam, and spam. In the words or Graham Chapman from the original skit… “can i just have the bacon, eggs, spam, and sausage without the spam”?
Years ago, I started tearing up the offers in my mailbox and mailing the shreds back to them on their own prepaid envelopes. I remember when unsolicited phone calls starting interrupting family dinners sometime in the 1980s with whatever they were trying to sell and whomever they wanted you to vote for or ask your opinion of. I suppose up until then, having a telephone was quite a technological advance and convenience. Now that so few people actually have land lines, I’d be willing to bet that we’ll look back at our cell phone habits during the last five years and wonder how we were tricked into paying so much attention. I’d argue that those little beeps and notifications on you phone are just another form spam trying to get you engaged exactly the same as the unsolicited, cleverly designed to look official, mail in your mailbox trying to get you to buy insurance. In the case of a smart phone, you’ve volunteered to carry around your mailbox whereas I’ve never volunteered to share my physical address, email address, or phone number with any unsolicited contact.
It’s all in the fine print on your order form, internet service provider, cellular provider contracts, and about every other form that asks for your information. I once maintained a bunch of databases related to education at a job I was working which were collected as an educational resource. One of the vendors at a conference outright offered a dollar amount for access to our databases. I informed the vendor that I was unable to do that and then a week later a coworker emailed me asking for copies of the personal information in them. I was like… “hey… we can’t sell those people’s data without their permission”. That’s exactly what happens all of the time and it’s how you end up getting spam emails, phone calls, mail, and text messages. Vast information systems on people like those used by credit reporting agencies are big business reaching much further than you may realize through various subsidiaries. Internet ‘information’ companies have become the largest businesses ever because they easily cross national boundaries. The Computing-Tabulating-Recording Company’s7 punch cards used by Nazi Germany were part of the foundation of IBM. We’re the product and we trade our information for currency. I voluntarily do it all the time for discount pricing and I have an email account stocked with follow up offers from those companies trying to re-engage me.
Fundamentally, there is a difference between the information I voluntarily offer and that which is traded without my consent. If I pay for a service, then why would you sell my personal information or allow others to abuse the service on top of what I’m already paying to make that service worse. I suppose there’s a well calculated and researched ‘line’ in which they over-monetized or spammed to make the service unattractive. Now there’s even a little spam machine, a tv screen with blaring audio, when you go to the gas station. I’m still going to that station because I trust that brand of gasoline, but at what point does it become completely normalized to bombard you with spam. I’m not going to even touch the internet side of social media spam. Regardless to say, I’ve done some legal spamming myself. I used to send out tens of thousands of real estate marketing emails. It was spam even though I got the email address legitimately by joining the multiple listing services. At that time, I don’t even think many real estate agents understood that it was spam at the time. I also once pitched an idea to a publishing company that owned thousands of billboards to network them to change the digital displays based on information like the weather to get more engagement. I was trying to capitalize on the information age and our psychological propensity to want to be ‘informed’. It’s how the newspaper industry has operated for several hundred years. William Randolph Hearst made a fortune publishing dirt on as many names as possible while famously saying “The news is what they don’t want you to print. Everything else is just ads”8.
I picked up an interesting tidbit while watching The Social Delimma9 last week. Tristan Harris10 compared the psychological manipulation used by online social media to magic. I’ve always had a thing for sleight of hand and magic tricks. Perhaps, I’m more keenly aware of the hand behind the back or out of sight. I’ve previously documented my take on and attempts to subvert those online algorithms.11,12,13,14 In these cases, I think the majority of the ‘room’ is still in awe of the trick. I can’t help but to worry about the kids today who will have shared access to much more data and I think it’s very likely that their aptitude will be a data point alongside of their address and phone number. At least the little screens have taken our attention are only in our pockets and attached to our wrists. Although Google glasses died, Facebook announced a partnership with Ray Ban to have glasses next year15. It reminds me of this video I had bookmarked four years ago where the implications for attention economy spam are visualized… literally.
Aside from the junk mail and calls, the very serious side of spam is social engineering, identity theft, and scams. Those scams don’t work if they emailed one person at a time. They rely on the fact that only 1 in 100,000 is a sucker. Identity theft should be called something else…. they’re not stealing my identity. They’re stealing a social security number, maiden name, and an address. We could fix that easy with a pin number attached to our social that could be changed online. I’ve always believed that it shouldn’t be my financial responsibility if someone take out credit in my name after stealing my personal information from somewhere else. The liability should fall on the bank issuing the credit and whomever else is responsible for not protecting my information. Data breaches are very common and you likely have a vulnerable email account right now. You can check at https://haveibeenpwned.com/16. It’s not just data related to an email address either. There should be a clearing house site for who has any of my other personal data and it should be tightly regulated by our systems of government in the same way that HIPPA & FERPA provide privacy for medical and educational records17,18. Shouldn’t we also have privacy rights on who are friends are, where we live, our sexual orientation, and our belief systems? These are not an unreasonable questions for our us to consider for policies. In 2014 the financial consequences of identity theft surpassed fifteen billion dollars19. Although I doubt the text message spam I received last weekend will be on any agenda anytime soon, I think we’ll eventually regulate personal data more strictly in an attempt to rectify financial losses.
No, I can’t stop your spam, but I can give you a couple helpful tips. Get a throwaway email account that you only use to register non-essential accounts. Don’t use your primary account on non-essentials. Get a second phone number from Google Voice, Burner, or any number of other text apps. Block unwanted calls. Join the Do Not Call Registry (even thought that seems to be doing little for me right now). Monitor your credit. Put your ringer on silent for unknown callers. Tear up unsolicited mail and send it back to them in their prepaid envelope. Use call blocking apps. Contact your service providers to see what they offer. Use the mark as spam tools in your email clients. Contact the same politicians that are contacting you and ask them to pass more stringent legislation. I’ll link to a couple of other basic resources below20,21. I remember back when I wrote the first “No, I Can’t Stop Your Spam” post. I used to literally pick up the phone and call the companies sending email spam asking for the evidence that the way they acquired my email address. There was also a time I would spam them back. If a company sent me an unsolicited email, I would add all of their employee email addresses to an automated list that would email them once an hour with various random emails. I sometimes joke with friends about rendering their phone numbers or email addresses useless if they spam me. Nowadays, I’m pretty good about ignoring in the attention economy, but on occasion, I still like to let spammers know that I can cheaply automate a spam campaign back against them with text messages, emails, mail, and recorded phone calls. It’s not exactly brain surgery. I’ve suggested a possible solution for social security number theft and I think that would work with domains and phone numbers too. Even the USPS could help out by charging more money to sent bulk mail or a certain size. In order to spam me, I must give consent via written permission22. Although I’m pretty tempted to start texting Lindsey Graham’s staff messages this afternoon with links to this article, I just reported the campaign texts to the Federal Communications Commission as they’ve suggested I do23.
- No, I Can’t Stop Your Spam – https://davidawindham.com/no-i-cant-stop-your-spam/
- No, I Can’t Stop Your Spam Revisited – https://davidawindham.com/no-i-cant-stop-your-spam-revisited/
- U.S. Do Not Call Registry – https://www.donotcall.gov/
- Reuters Trump to Shut off TikTok and WeChat Sunday – https://www.reuters.com/article/us-usa-tiktok-ban-exclusive/trump-to-shut-off-tiktok-wechat-to-new-u-s-users-on-sunday-idUSKBN2691QO
- Spamming – https://en.wikipedia.org/wiki/Spamming
- Monty Python Spam, Spam, & Spam – https://en.wikipedia.org/wiki/Spam_(Monty_Python)
- Computing Tabulating Recording Company – https://en.wikipedia.org/wiki/Computing-Tabulating-Recording_Company
- William Randolph Hearst – https://en.wikipedia.org/wiki/William_Randolph_Hearst
- The Social Delimma – https://en.wikipedia.org/wiki/The_Social_Dilemma
- Tristan Harris – https://en.wikipedia.org/wiki/Tristan_Harris
- Dirty Algorithm – https://davidawindham.com/dirty-algorithm/
- Data Mining Our Viewing Habits – https://davidawindham.com/data-mining-viewing-habits/
- How Does a Website Know My Name – https://davidawindham.com/how-does-a-website-know-my-name/
- Facebook Weirdness – https://davidawindham.com/facebook-weirdness/
- Facebook Ray Ban Smart Glasses – https://variety.com/2020/digital/news/facebook-smart-glasses-ray-bans-essilorluxottica-1234772183/
- Have I Been Pwned – https://haveibeenpwned.com/
- HIPPA – https://en.wikipedia.org/wiki/Health_Insurance_Portability_and_Accountability_Act
- FERPA – https://en.wikipedia.org/wiki/Family_Educational_Rights_and_Privacy_Act
- Financial Consequences of Identity Theft: Evidence from Consumer Credit Bureau Records – https://philadelphiafed.org/-/media/research-and-data/publications/working-papers/2019/wp19-02.pdf
- C-NET How to Stop Robocalls – https://www.cnet.com/how-to/stop-annoying-robocalls-to-your-phone-using-every-trick-we-know/
- USA Today How to Block Robocalls – https://www.usatoday.com/story/tech/columnist/komando/2019/02/07/no-more-robocalls-how-block-unwanted-calls-iphone-android/2778059002/
- Federal Communications Commission Avoiding Spam – https://www.fcc.gov/sites/default/files/avoiding_spam_-_unwanted_email_and_text_messages.pdf
- Federal Communications Commission Consumer Complaint Center – https://consumercomplaints.fcc.gov/hc/en-us